Stefan Kostić, CEO of IPification, the company that offers IP-based mobile authentication and fraud prevention solutions, discusses the recent hack of popular cryptocurrency platform Coinbase where some 6,000 customers had their assets stolen via an exploit of the company’s SMS authentication security. What happened, how did the hackers do it and what can we learn from the failures?
You didn’t have to be in the cybersecurity industry to hear about the huge Coinbase hacking in the last few weeks. Because the number of cyberattacks isn’t going down any time soon, we have the responsibility to learn from this incident.

With the pandemic, the number of online activities has reached record highs, but so has cybercrime. To illustrate, when compared to 2019, eCommerce transactions increased 40% across 850 US retail eCommerce domains, while phishing attacks have seen a 350% increase from January to March of the same year.
Let’s first assess this incident.
Behind the Coinbase Hacking
The cybercriminals infiltrated accounts and stole cryptocurrency from approximately 6,000 Coinbase customers. How? Reportedly, they exploited a multi-factor flaw — or SMS two-factor authentication flaw, to be more precise.
In order to take over an account via SMS 2FA, the attacker would need to know the user’s Coinbase account email address, password, and phone number. This data could have come from a past data breach, or via a phishing campaign that Coinbase says targeted their users between April and early May 2021.
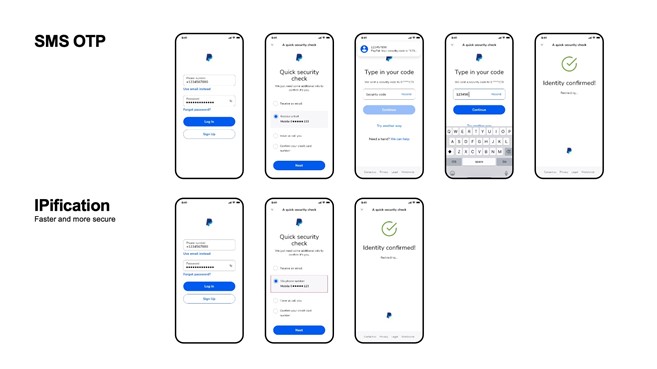
This design flaw can be exploited for rerouting or intercepting an SMS containing your SMS OTP, enabling cybercriminals to take over your account… the reason that tech giants like Microsoft, Google, and Apple are choosing to move away from it.“
Usually, SMS 2FA would protect you here (to some extent), but there was a flaw with the company’s SMS account recovery protocols.
What this SMS 2FA Coinbase flaw is, we don’t know.
But, it’s important to remember that SMS 2FA comes with many risky flaws that aren’t specific to the Coinbase platform — which is why the company only recommends it as a last resort, even after their flaw was fixed.
SMS 2FA – From A Security Hallmark To A Modern Vulnerability
In the early days, SMS 2FA redefined how we viewed mobile security. As we started imposing stricter rules for passwords, we added an additional layer of security, protecting our accounts better than we had ever before.
However, we have to remember that even then, SMS 2FA has its own issues — some of which present since the very inception of the SMS technology.
Such is the SS7 switching protocol which has been a feature of SMS since 1975 when it was originally introduced. This design flaw can be exploited for rerouting or intercepting an SMS containing your SMS OTP, enabling cybercriminals to take over your account.
That right there is one of the main reasons that experts have been calling for replacing SMS 2FA for years now, and the reason that tech giants like Microsoft, Google, and Apple are choosing to move away from it.
Furthermore, using SMS 2FA puts you at risk of SIM swapping. To pull it off, fraudsters only really need your personal identifiers like your first and last name, social security number, DoB, or your ID — most of which they could acquire through a phishing attack or a data leak.
This will sound scary, but it’s important to know: 80% of all SIM swap attacks are successful, which is why mitigating this risk should be a priority.
Finally, SMS 2FA doesn’t have an ideal user experience. Typing in your phone number, waiting for that SMS, putting it back in… It’s a hassle, and it’s why 64% of users refuse to use SMS 2FA, many of them reverting back to just passwords.
Moving Forward Without SMS 2FA
What are the alternatives? 2FA Authenticator Apps, biometrics, and SIM card-based authentication options.
Authenticator app 2FA offers significantly higher security than SMS 2FA, but the user experience deteriorates even further. The users are now required to completely quit one app, open the authenticator, generate a code, copy it, get back into the original app, and only then sign in. Companies seem to like it, but the users don’t — and this is a huge factor as user experience is becoming the most significant competitive advantage.
On the other hand, biometric authentication is the strongest when it comes to user experience, but it also comes with privacy concerns. Different hardware providers develop this technology in different ways, and remember, you can always reset your password but changing your fingerprint is just a tiny bit harder.
In 2021, users shouldn’t have to choose between security, user experience, and data privacy. They can have all three, and this is actually possible through SIM-based authentication methods, that put the mobile ID key back where it is the most powerful – in the hands of mobile network operators.
As an example of how it would work, it’s how we’ve developed IPification.
IPification assigns each user their own unique mobile ID key, created from the user’s phone number, SIM card, and device data passed via the user’s public IP address and port, ensuring security and data privacy. And all it takes to authenticate is one click.
To ensure our users are safe, we have to get them to use additional security. And to get them to use additional security layers, we have to provide a seamless user experience.