Michael Becker Interviewed Drummond Reed, Chief Trust Officer at Evernym, an Avast company. They discussed the future of the personal data and identity marketplace.
In this marketplace, the data subject – you, me, the individual, private and public institutions – will soon be in control of their personal data and identity. Through the self-sovereign identity (SSI) approach to data management, businesses and people will redefine the organization-individual relationship. In an SSI-powered future, trust will be restored between both parties along with the exchange of mutually beneficial value.
We are making the industry more efficient, more trusted, more secure, and more successful. – Drummond Reed, Chief Trust Officer, Evernym
The message is clear: “The future is here and on its way to even distribution.” That is what came out, loud and clear, during my conversation with Drummond Reed, Chief Trust Officer at Evernym.
Drummond and I sat down to discuss the personal data and identity marketplace and specifically, its future. In this future, the data subject – you, me, the individual, private and public institutions – is in control of their personal data and identity.
This idea is not based on some futuristic sci-fi movie plot; rather it is grounded in real, industry-standard technology (often referred to as the self-sovereign identity (SSI) approach) that is actively supported and being rolled out by enterprises and governments around the world. SSI promises to redefine the organization-individual relationship. It has the potential to have a bigger impact on society than the introduction of the Internet. It will systematically re-introduce trust into digital engagements, which in turn will transform business models, create wealth, reduce costs, and save lives. It sounds far-fetched, sure, but it’s not. It is here. It is real. And its use will be as common as the web browser in a few years.
The Internet and Posture of Distrust
A prosperous and efficient society is built on trust. We rely on trust to safely and efficiently engage in offline and online interactions with people and machines. Simply put, trust is having confidence in the honesty and integrity of another. That is to say, we have trust when we accept that the identity assertions and information provided to us by another are accurate, verifiable, and factual (when this is not the case, we don’t call it trust – we call it faith).
Businesses can trust because they have the tools to verify the individual’s assertions. If they are not using these tools, then they are working under faith, not trust. And, individuals’ have faith that the businesses will professionally render their services and properly handle and safeguard their identity and billing information.“
The distinction between trust and faith is one of the market failures of the Internet. There is very little trust in the internet; there is a lot of faith. We often talk about trust on the internet, but what we’re really talking about is faith. As noted above, to build and maintain trust, one should be able to verify the assertions made during an interaction. Since individuals do not have the same capabilities that organizations do to verify and validate the assertions that an entity they’re interacting with is making in real-time, what people have is faith and not trust. That faith is backed up by the social contract, commercial contracts, and regulations, true, but this is not really to trust but reinforced faith.
For example, when boarding a plane, renting a car, or checking in at a hotel, the businesses’ individuals interact with trust that the proof of identity they provide (e.g., their driver’s license or ticket) is accurate, factual, and verifiable. That is to say, it represents who they say they are and that they fully intend to pay their bills with their supplied payment methods. Businesses can trust because they have the tools to verify the individual’s assertions. If they are not using these tools, then they are working under faith, not trust. And, individuals’ have faith that the businesses will professionally render their services and properly handle and safeguard their identity and billing information. Thankfully, for the vast majority of interactions that people have online and offline, the faith they have is well-founded, but this is not always the case.
Why is this not the case? The intentions of each party in any given interaction may not be mutually well-understood or aligned. Just try reading the average terms and services and privacy policy today. It’s difficult; the average person has trouble reading them. The fact that the fine print empowers businesses to use or source an individual’s personal data and identity from third parties is not always clear (just think of the surveillance economy). Also, unintentional human error and technical glitches happen all the time, which inadvertently expose people’s data and identity, which in turn exposes them to potential harm. Finally, and sadly, not everyone can be trusted, as evidenced by the rampant growth in cybercrimes being perpetrated throughout the world.
The Internet was built with the best of intentions. It was built with the vision of equality and enabling the free flow of information to enhance collaboration and exchange. However, the Internet has drifted from this North Star over the years. Today, savvy and well-informed Internet users know this. They approach the Internet with a posture of distrust rather than trust. They are aware of the surveillance economy, and that industry is making billions from the free flow of personal data and identity. They understand that phishing attacks, e.g. fraudsters representing themselves as someone else and trying to steal sensitive information, are on the rise. And, given this awareness, they take action.
They install malware and antivirus protection, use tracker blockers, obfuscate their personal information, and take any number of other actions to protect themselves. Likewise, the savvy business is forced to maintain a security posture, like introducing friction such as multi-factor authentication into the customer experience and doing whatever else to counteract the threat of fraud and other malfeasance. We can do better. The posture of distrust that everyone must take is tragic. It is inefficient. It is costly.
Luckily, personal data and identity thought-leaders and leading organizations, like Drummond and Evernym, have a solution – self-sovereign identity.
Reestablishing Trust Online With The Self-Sovereign Identity Approach
We are about enabling digitally trusted relationships. – Drummond Reed, Chief Trust Officer, Evernym
Today, a fundamental flaw on the Internet is that we can’t trust it, especially when it comes to personal data and identity. As Tim Berners-Lee notes: “we’ve lost control of our personal data.”
Leading technologists, privacy, policymakers, human rights advocates, and more have been working on a new approach–self-sovereign identity (SSI)–to reestablish trust on the Internet and solve the problems of personal data management (including personal identifiers, which are sets of identifiers used to establish an individual’s identity) for the last couple of decades. This approach is just now reaching adolescence and making its way into the global market.
Drummond explains that the primary goal of SSI is to bring trust back to the Internet by enabling individuals and enterprises to use digital credentials to simplify and streamline the Internet’s digital identity management and personal data exchange process and related experiences, such as onboarding with a company and transacting over the Internet. The idea is that trust can be rejuvenated by making these processes and experiences more secure and verifiable with less work on the side of the individual and, in the long run, the enterprise.
For instance, with SSI-powered experiences, no longer will people need to create, remember, and use usernames and passwords; all they’ll need is their SSI digital wallet. No longer will they have to fill out long forms; they can maintain a persona – a digital profile – to automatically provide whatever information that is needed for the situation at hand from their SSI digital wallet. No longer will the enterprise have to spend billions to fight cybercriminals, they’ll be able to use these savings to invest in innovation and serving their customers. These are just a few things the SSI has the potential to make true. There is so much possibility when we can drop the posture of distrust and take on the posture of trust.
It is still in its early days, Drummond says, but he puts forth that “the introduction and adoption of SSI will change society as much as the introduction and adoption of the web did.”
Defining Self-Sovereign Identity Terminology
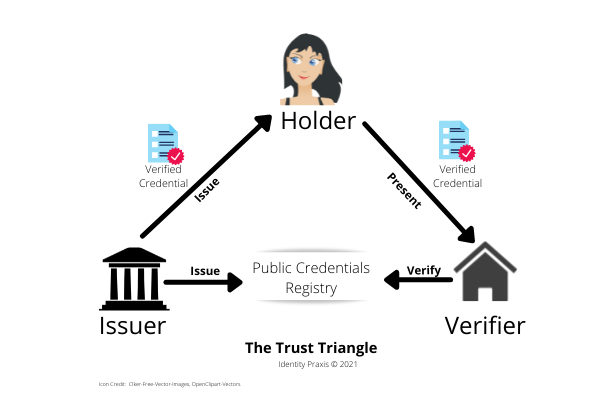
Self-sovereign identity is a technologically grounded approach for establishing trustworthy digital connections and relationships between parties engaging over the Internet (i.e., via computers and mobile devices, in both online and offline situations) so that they can engage in trusted transactions. At all times, each party maintains and has granular control over their personal data and identity. SSI, with cryptographic certainty, ensures that—through the “Trust Triangle”—each party knows who they’re dealing with. The Verifier can be assured that the data or identity assertion (i.e., verifiable credential, aka authentic data) being presented by the Holder is authentic since the information (aka Verifiable Credential) being presented has been verified by the Issuer.
Let’s unpack this definition of SSI and outline some key terms:
- Issuer is the party that produces and certifies that the information represented in a Verifiable Credential is authentic and accurate.
- Holder is the individual issued a Verifiable Credential and who has the authority to use it by virtue of being in control of it and having the means (e.g. SSI Digital Wallet) to share all or part of the credential.
- Verifier is the party receiving a Verified Credential and looks to validate, aka verify, the credential’s authenticity validity (e.g., the driver’s license could be authentic, but is no longer valid because it expired).
- Verifiable Credential is an open digital standard for representing an information item or an information set that can be verified as having been published by an Issuer. For example, the information items (e.g., ID number, date of issuance, name and location of the Issuer, the name of the person it was issued to (aka the Holder), the birthdate and address of the Holder, etc.). The Information Set is a collection of information items, like all the information on a driver’s license or in a passport. Information items and sets can be further deconstructed by the SSI Digital Wallet or serviced down to verifiable insight without the disclosure of any more information that is necessary, e.g., “Is the individual 21?” or “Is the password valid?” In these examples, the Verifier does not need the individual’s complete birthdate or all the information on the passport as long as they can trust that the insight shared is accurate and factual.
- Authentic Data is another term (coined by Dave Huseby (2021)) to refer to Verifiable Credentials. Dave argues that the use of the term “credential” is limiting, as it makes one think solely of driver’s licenses, passports, tickets, and other credential-like information. He rightfully points out that the self-sovereign identity approach can be applied to any data, not just identifiers and credentials. So, authentic data refers to any data that the Issuer can verify.
- Trust Triangle represents the three parties—the Issuer, the Holder, and the Verifier–in a self-sovereign identity (SSI) organized relationship. The Issuer issues a Verifiable Credential. It provides the private key to the Holder and places a public key in the public register. When the Holder wants to assert their identity or present some information, the Holder will present all or a portion of their credential to the Verifier. The Verifier can then verify the authenticity of the assertion against the public registry. All of this is managed using state-of-the-art decentralized data storage and data cryptology. Note: An individual or enterprise can play dual roles. For instance, in the case of airlines, the airline issues a ticket to a Holder. The airline will also act as the Verifier when the hold is checking in. When the Holder is going through airport security, the airline will still act as the Issuer, but the security authority will be the Verifier.
- SSI Digital Wallet is a self-sovereign identity (SSI) application that resides on a phone or computer (in some instances it may be referred to as a personal data store, or personal information management system). Analogous to the traditional physical wallet, the SSI Digital Wallet will store identification cards (e.g., driver’s license, passwords), health insurance IDs, banking cards, loyalty cards, membership IDs, vaccines status cards, cash cards, and all kinds of other forms of identification and information (receipts, photos, notes, etc.). The SSI wallet differs from the physical wallet in that all the information stored in the wallet is cryptographically secure so that only the wallet owner (aka Holder) can access and use the credentials.
Self-Sovereign Identity In Action
We are far beyond the theoretical now, we [the industry] are delivering solutions. – Drummond Reed, Chief Trust Officer, Evernym
During our conversation, Drummond highlights and alludes to the following SSI proof points to prove a point: “We are far beyond the theoretical now, we [the industry] are delivering solutions.”
SSI Deployment Use Cases
During our conversation, to prove his point, Drummond highlights and alludes to the following SSI proof points. I will add my own: Evernym was purchased by Avast in December 2021. Avast is one of the largest cybersecurity players and is part of the NorthLifeLock family. It should not be too long until we see more consolidation in the industry and more practical use cases out there in the wild.
Real-Life SSI Use Cases. There are many real-life SSI use cases that are being rolled out on a global scale.
- IATA Travel Pass Initiative This is an initiative developed by the International Air Transport Association (IATA), which is the trade association for the world’s airlines, representing some 290 airlines or 83% of total air traffic.
- Ontario Digital ID
- EU Support for SSI by Sept. 2022 The EU Commission in June 2021 announced that it has targeted September 2022 for every EU Citizen to have the option to obtain an SSI-based digital identity.
- Estonia e-Identity Estonia has pioneered digital ID for its citizens, with 99% of public services being available online and 98% of all tax declarations being filed electronically. Interoperability is all enabled by voting online, e-residency, cryptocurrency, and private-public systems. The government has developed blockchain infrastructure (a foundational element of SSI) to protect itself and its citizens.
- The United Kingdom National Health System UK National Health System (NHS) has introduced the Digital Staff Passport, which will allow staff to freely move between hospitals, saving administration fees. Drummond Reed suggests that this will not only save time (roughly 40,000 hours) and money but will save lives. He notes that practitioners will have more time for patients, now that they don’t have to spend this time on paperwork.
Note: A useful source for self-sovereign identity industry insight is a blog—Identosphere Blogcatcher maintained by Kaliya Young and Infominer. It aggregates the blogs of hundreds of leading self-covering identity companies, initiatives, and thought-leaders.
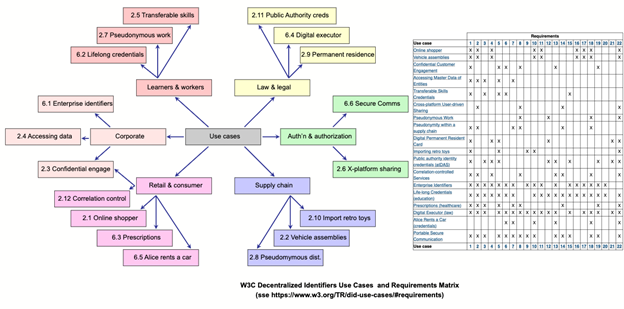
Theoretical SSI Use Cases. In addition to the above practical self-sovereign identity use cases, eighteen theoretical self-sovereign identity use cases, and the technical requirements needed to execute them, can be found in the W3C Decentralized Identifier Specification.
There has never been a connection this strong in human history that will be this persistent. – Drummond Reed, Chief Trust Officer, Evernym“
New Business Metric: Number of Unique Connections
One of the most important insights I gleaned from my conversation with Drummond was this: SSI will fundamentally change how businesses will measure the connections and relationships they have with individuals.
Business uses various direct and indirect methods to establish a relationship and stay connected with individuals. The identifiers used to stay connected with individuals vary as the individuals’ relationship with businesses evolves. Identifiers are used for advertising engagement, customer identity management (identification, authentication, verification), anti-fraud and anti-money laundering compliance, media asset tracking, business entity tracking, maintaining brand safety, privacy management, user experience management (inc. personalization), communication, media engagement measurement, and attribution, to name a handful.
Common customer identity management identifiers include cookies (which are being deprecated), user single-factor and multi-factor authentication (e.g., username and passwords backed up by SMS OTP, authentication apps, or biometrics), government-issued IDs, physical addresses, phone numbers, email addresses, credit cards numbers, and more.
When using identifiers to track and engage individuals, enterprises must contend with various technology, connection persistence, privacy, security, identity management, regulatory compliance, and related challenges. Focusing on just one of these is a most challenging problem for business. People move. In the U.S., for instance, 10% of the population moved in 2019. Phone numbers go bad. Emails degrade (roughly 22% of emails degrade in a year), and most recently, individuals have started to adopt alias emails to block their real identity. You get the point – it is hard for a business to stay connected with an individual.
In our conversation, Drummond remarked: “There has never been a connection this strong in human history that will be this persistent.” What Drummond is referring to is the DID, otherwise known as the decentralized identifier. The DID is a core element of the SSI experience. The DID is ugly. It is a long string of numbers that would mean nothing to anyone. Luckily, unlike email or phone numbers, the actual DID string itself is handled by the SSI applications, not the enterprise or the individual. Here is what one looks like:

When an individual and a business connect via the self-sovereign identity approach, they share their respective DIDs. The connection between the parties will remain persistent as long as either party does not revoke their connection. Only the valid holder of a DID can use it, and therefore verifiable certainty of the relationship between the enterprise and the individual can be established.
In the future, Drummond suggests that these connections will become the primary measure of business success, especially in marketing and advertising. For instance, today marketers use metrics like likes, media impressions, email opt-ins, SMS opt-ins, etc. These measures are fine, but ephemeral and lack the personal control that DIDs offer the individual. DIDs, however, are persistent and under the individual’s control.
Again, the only way a business can obtain an individual’s DID is if the Holder provides it. Businesses won’t be able to go to data brokers and buy DIDs, as they do with email addresses today. Moreover, as soon as the Holder is ready to move on, the Holder can revoke it. Therefore, when a business reports on how many “direct connections” they’ve established with individuals, this number will mean something. It means that people have connected and stayed connected with a business of their own volition. This is a game-changer. It means that businesses will be incentivized on a legit metric and forced to focus on building and maintaining real relationships (not fake bot accounts) and provide value if they want to keep their metrics up.
Where do we go from here?
I have little doubt that the self-sovereign Identity approach will take hold and be mainstream at some point in the future – three, four, five years from now, if not sooner. We are still in the early days, but unlike the introduction of the web, which was completely new at its introduction to the world, self-sovereign identity is being planted in fertile ground. So be forewarned, it is going to grow fast.
Drummond notes, “We forget that it took years for the web to settle down to the expectation that it ‘Just works,’ so it will take time for self-sovereign identity. However, as businesses integrate it into their systems and people see the value, magic will happen. People will begin to say, “I know who I’m connecting with. They know they’re connecting with me. We can drop the defensive posture,” Drummond says. Once we drop our defensive posture, a new kind of trusted relationship will emerge. More data will flow, and businesses and individuals alike will be in a position to create more and more value for themselves and each other.
We’re on the verge of the next revolution. Let’s get ready.