Recent draft NIST guidelines on digital authentication suggested the depreciation of SMS based 2-factor authentication (2FA). Here Rob Malcom of Mblox & CLX, takes a deep dive into what the proposals mean, and how they may cause 72% of Americans to fail to adopt 2FA at all.
I went on vacation a few weeks ago and returned to a world seemingly in panic over the draft NIST Guidelines on Digital Authentication and its deprecation of SMS for use in 2-factor authentication. After reading countless articles I was disappointed at the apparent media frenzy with their circular reasoning and lack of fundamental research required to outline the true risks and implications of this proposal to businesses and consumers.
The risks of using SMS in 2FA identified by NIST are not widely understood and I would have liked to see far more emphasis on what can be done to mitigate these risks without assuming that SMS will at some point be removed from 2FA altogether.
It is interesting that much of the publicity and attention has been on SMS, but many (if not all) of the weaknesses with SMS are identical for voice and as such deprecating SMS would most likely lead to the deprecation of voice in time too.
Credit must go to John Fontana for Identity Matters (ZDNet), Violet Blue(Engadget) and Michelle Maisto (eWEEK) for at least calming the frenzy and bringing some clarity to the debate. Credit must also go to Paul Grassi from NIST for writing a blog outlining the reasons for their draft decision which went a long way to calm the nerves of many.
In this blog, I will argue, that whilst SMS has some weaknesses, it is the only out of band authentication type with the ubiquity and convenience that could have driven the adoption of 2FA by mainstream, non-technical users so fast over recent years. I believe that deprecating SMS now will lead to slower adoption of 2FA across all Authenticator Types and inhibit reaching NIST’s overall objective, which is to encourage businesses to always use 2FA.
Ease of use and convenience is by far the most important aspect of 2 factor authentication adoption and SMS leads the pack in terms of overall adoption for this reason.
As we know from recent media stories the fundamental email address combined with password (memorized secret) combinations are extremely weak. Adding 2FA (regardless of Authenticator Type) significantly increases security; so it is no surprise that NIST would like to see this become a reality.
In this blog I will attempt to break down the discussion into something that is better structured and researched and just in case you don’t want to read the whole thing, the conclusions are as follows:
- The NIST suggestion to deprecate SMS is premature and will damage the overall adoption of 2-factor authentication by businesses and users alike.
- Not offering SMS as a 2FA alternative to time-based one-time password (TOTP) applications will make it extremely difficult and costly for businesses to deal with users who have had their devices lost or stolen.
- Only 79.1% of US subscribers currently have a smartphone, of which more than half only download an app very very rarely. This leads us to conclude that, without SMS, more than 72% of Americans will be stuck without a viable 2FA solution.
- The weaknesses of SS7 and SMS are exaggerated when trying to attempt a remote hack en-masse and consequently mobile operators should focus on securing their networks and proving to NIST that these intercept risks have been resolved.
Firstly, who is NIST? Some international readers may not be familiar with who they are and what they do. Basically they are “a measurement standards laboratory, and a non-regulatory agency of the United States Department of Commerce.” An important point here is that they encourage businesses to follow the standards they set, but they cannot force anyone to adhere to them.
The US Federal Government however may be required to comply with their standards
Secondly, it should be noted that the NIST guidelines are currently in DRAFT form and anyone who wishes to make comments can do so here. It’s likely that the final recommendation will only take place early next year.
I’ve created a diagram to try and explain the rationale by NIST to propose deprecating SMS from two-factor authentication.
In summary, NIST wants to deprecate SMS for use in 2-factor authentication because a.) more secure methods (albeit less convenient) exist, and b.) SMS is perceived as being insecure largely because of the amount of recent press articles discussing the weaknesses of SS7 that have found their way into mainstream media.
Are there more secure methods than SMS 2FA without losing the convenience?
It is important to emphasise that ‘deprecate’ in this context is not banning or disallowing but rather recommending other methods are used in its place. Paul Grassi writes on the NIST blog that they simply want to discourage the use of SMS because “you can use this puppy for now, but it’s on its way out.”
There is no denying that more secure methods do exist provided that the user is willing to download a TOTP or other app and configure that app to work with a particular service. This seems unlikely to be done across mainstream, non-technical users for the reasons cited below.
For the purposes of this blog I will assume that all smartphones are protected by at least a 4 digit pin (or fingerprint) and that in the event of a phone being lost or stolen it will be reported very quickly after the fact so as to ensure that the SIM card is rendered useless. The security implications of this not being the case is therefore out of scope of this blog.
If we assume this to be true then a fundamental issue with the TOTP method arises when you lose your device or get a new one as I recently discovered; The only way that I could access my personal email on Google (which had 2-factor authentication enabled) was to use SMS, as I needed to have access to my account before I could re-configure my Google Authenticator app on my new device.
Without SMS I simply would not have been able to access my account without going through a 3-day process with Google to prove that I had lost my device. I therefore conclude that both should be used as a backup for the other and that SMS plays a fundamentally important role in this use case.
Furthermore this method, albeit more secure, is no silver bullet for replacing SMS entirely.
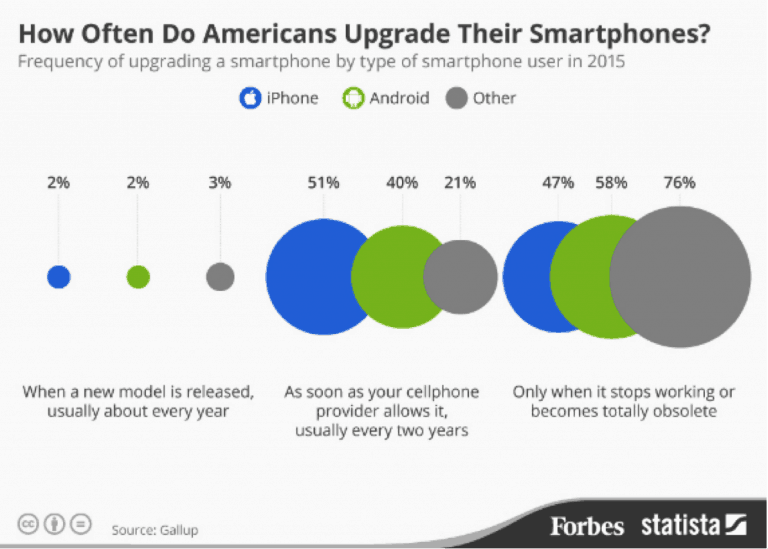
As you can see from the Forbes / Statista (Source: Gallup) study in 2015, users are most likely to change their phone every two years, which on a rolling basis, is around 8.3 million people per month changing their device; this is a vast amount of people who will discover their TOTP app cannot easily be transferred to another device without SMS 2FA.
We have seen similar co-dependencies in the world of OTP messaging apps whereby apps such as Viber, Whatsapp etc., use SMS and Voice to validate and map a device to a telephone number. Given that SMS should always be used as a backup, then the overall security of a service will always be only as strong as SMS, and to that end I would far rather have mobile operators focus on increasing the security of SMS in 2-factor authentication by installing firewalls than encourage businesses to disband it.

It should also be noted that TOTP apps are more secure they are still vulnerable to attack just like any software, and which ever TOTP app you use, you need to make sure they are trusted to keep it updated (without losing service configurations) and will be in business for perpetuity or you risk leaving all your users stranded and having to ask them to change their authenticator app at some point.
CLX / Mblox


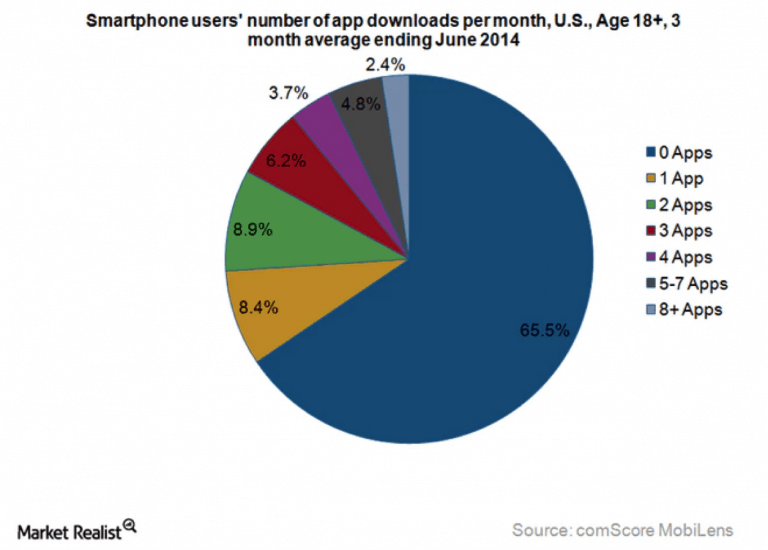
Lastly, looking at the number of US mobile phone subscribers that have a realistic chance of actually downloading at TOTP app; We forget that not everyone in the world has a smart phone and as a consequence using SMS again becomes the best method for these users. Comscore currently believes US smartphone penetration sits at 79.1%, leaving nearly 21% of the population unlikely to use any mobile based out of band authentication type (except SMS).
This however is not the whole story, as the number of users that ever download an app on their smart phone is extremely low, with 65.5% of those users hardly ever downloading an app. Which means that 72% of the US population are unlikely to ever download an alternative to SMS 2FA.
Part 2 of this post will appear on the MEF minute tomorrow
Sign up now to MEF’s Mobile Messaging Programme – The Future of Messaging. A cross-ecosystem approach to accelerate market clean-up and advance innovation. Find out more and download the free A2P messaging fraud framework now